Private VLAN
|
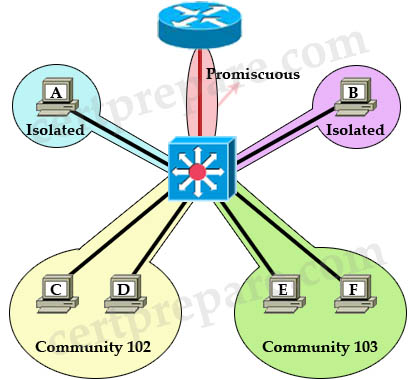
Quick review: The main purpose of Private VLAN (PVLAN) is to provide the ability to isolate hosts at Layer 2 instead of Layer 3. As you know, a VLAN is a broadcast domain, by using PVLAN we are splitting that domain into some smaller broadcast domains. For example, without PVLAN, a service provider wants to increase security by isolating customers into separate domains so that they can’t access each other, they have to assign them into different VLANs and use different subnets. This can result in a waste of IP addresses and difficulty in VLAN management. Private VLANs (PVLANs) can solve this problem by allowing the isolation of devices at Layer 2 in the same subnet. PVLAN can be considered “VLANs inside VLAN”. There are three types of ports in PVLAN: * Isolated: only communicate with promiscuous ports. Notice that it cannot even communicate with another isolated port. Also, there can be only 1 isolated VLAN per PVLAN.
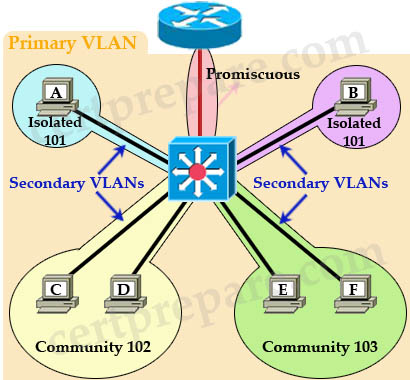
For example, in the topology above: + Host A cannot communicate with Host B, C, D, E and F. It can only communicate with Promiscuous port to the router. Notice that even two Isolated ports in the same VLAN cannot communicate with each other. + Host C can communicate with Host D because they are in the same community but Host C cannot communicate with E and F because they are in a different community. + All hosts can go outside through promiscuous port. Also I want to mention about the concept of “primary VLAN” and “secondary VLAN”. PVLAN can have only one primary VLAN; all VLANs in a PVLAN domain share the same primary VLAN. Secondary VLANs are isolated or community VLANs.
Configuration of PVLAN: 1. Set VTP mode to transparent Sample configuration used the topology above: //First set VTP to transparent mode //Create secondary VLANs //Create primary VLAN //Associate secondary (isolated, community) VLANs to the primary VLAN //Assign Promiscuous port to the port connected to the router, with the primary VLAN mapped to the secondary VLAN. //Ports connected to hosts A, B, C, D, E, F are configured in host mode and assign to appropriate VLANs (A and B to isolated VLAN 101; C and D to community VLAN 102; E and F to community VLAN 103): Switch(config-if)# interface range f0/3 -0/4 //connect to host C and D Switch(config-if)# interface f0/5 – 0/6 //connect to host E and F To check the configuration, use this command: Switch# show vlan private-vlan |
Question 1
Explanation
Before configuring private VLANs, we must set VTP mode to transparent because VTP version 1 and 2 do not support private VLAN (VTP version 3 does support PVLAN). Notice that a switch in VTP transparent mode still forwards other VTP updates to its neighbors.
Question 2
Explanation
There are three types of ports in PVLAN:
* Isolated: only communicate with promiscuous ports. Notice that it cannot even communicate with another isolated port. Also, there can be only 1 isolated VLAN per PVLAN.
* Promiscuous: can communicate with all other ports. The default gateway is usually connected to this port so that all devices in PVLAN can go outside.
* Community: can communicate with other members of that community and promiscuous ports but cannot communicate with other communities. There can be multiple community VLANs per PVLAN.
Question 3
Explanation
Isolated VLAN is a secondary VLAN and it can only communicate with the promiscuous port. Also, there can be only 1 isolated VLAN per PVLAN (although this isolated VLAN can be configured to many ports, but these ports cannot communicate with each other).
Question 4
Explanation
Promiscuous port: can communicate with all other ports. The default gateway is usually connected to this port so that all devices in PVLAN can go outside.
Question 5
Explanation
The default gateway is usually connected to promiscuous port so that all devices in PVLAN can go outside.
Question 6
Question 7
Question 8
Question 9



Question 10 does not make much sense. Can some one help please ?
Q10 Correct answer is indeed A.
* Isolated: only communicate with promiscuous ports. Notice that it cannot even communicate with another isolated port. Also, there can be only 1 isolated VLAN per PVLAN.
@Abdu
October 29th, 2019
Q1- Cisco has contradicting information :
here : https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst3750/software/release/12-2_55_se/configuration/guide/scg3750/swpvlan.html
it says : VTP version 3 does support private VLANs
and here : https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst3850/software/release/37e/consolidated_guide/b_37e_consolidated_3850_cg/configuring_private_vlans.pdf
it says : Private vlans are supported in transparent mode for VTP 1, 2 and 3. Private VLANS are also supported on server mode with VTP 3.
^^^
Vtp v3 can propagate pvlans to other switches in transparent/server modes, but if you view the show vlan private-vlan command, it will not show up as private vlans but they will show up IN THE VLAN option “show vlans”.
So, say I create Pvlans on switch one, primary server mode.
On switch2, I can see that the vlans are propagated(using the command “show vlan”, but the actual VLAN type (Pvlans) will not show up when you verify Pvlans using “Show vlan private-vlans”