VLAN Trunking
Question 1
Explanation
These errors are generated because the native VLAN is not matched on the two switches (the native VLAN on SW-1 is not the default native VLAN 1 while the native VLAN on the other side is VLAN 1). The errors indicate that spanning tree has detected mismatched native VLANs and has shut down VLAN 1 on the trunk.
We should verify that the configurations of the native VLAN ID is consistent on the interfaces on each end of the IEEE 802.1Q trunk connection. When the configurations are consistent, spanning tree automatically unblocks the interfaces.
Question 2
Explanation
In 802.1Q, the trunking device inserts a 4-byte tag into the original frame and recomputes the frame check sequence (FCS) before the device sends the frame over the trunk link. At the receiving end, the tag is removed and the frame is forwarded to the assigned VLAN. 802.1Q does not tag frames on the native VLAN. It tags all other frames that are transmitted and received on the trunk.
Reference: http://www.cisco.com/c/en/us/support/docs/lan-switching/8021q/17056-741-4.html
Question 3
Explanation
802.1Q is a industry standards based implementation of carrying traffic for multiple VLANs on a single trunking interface between two Ethernet switches. 802.1Q is for Ethernet networks only.
Question 4
Explanation
We can use the “switchport trunk allowed vlan ” to specify which VLANs are allowed to go through. Other VLANs will be dropped.
Question 5
Explanation
Manually configure trunking with the “switchport mode trunk” command and manually configure access interfaces with the “switchport mode access” prevent auto trunking on that interface.
Disable DTP with the “switchport nonegotiate” so that DTP messages are not advertised out of the interface is also a good way to prevent auto trunking.
Question 6
Explanation
There are two protocols that can be used for trunking: Inter-Switch Link (ISL) and 802.1Q. We can choose which protocol to run by the “switchport trunk encapsulation “. After that we can configure trunking mode with the “switchport mode trunk” command.
In fact this question is not clear and may cause confusion because Dynamic Trunking Protocol (DTP) is the protocol that can automatically negotiate for trunking.
Note: The DTP options can be dynamic auto, dynamic desirable, and trunk.
Question 7
Explanation
By default all VLANs are allowed to go through a trunk but if we apply the “switchport trunk allowed vlan ” then only these VLANs are allowed to go through, other VLANs are dropped so be careful when limiting VLANs on the trunks with this command.
Question 8
Explanation
We can use the “switchport trunk allowed vlan ” to specify which VLANs are allowed to go through. Other VLANs will be dropped.
Question 9
Explanation
First we will explain these two commands:
| switchport access vlan 10 switchport mode trunk |
The first command is used for an access port whist the second is used for a trunk so why are they here at the same time? In fact this interface was set as a trunk. The “switchport access vlan 10” is still there but it does not affect the operational mode of the port -> Gi1/0/1 is a trunk port so it will not appear in the “show vlan” command.
The “switchport voice vlan 11” command here only tries to confuse you. But it does have an effect on the port: Cisco uses CDP to specify a Cisco IP Phone and will automatically place that traffic into the voice VLAN. For example if we configure like this:
| interface fa0/0 switchport trunk encapsulation dot1q switchport mode trunk switchport voice vlan 11 |
Then the voice traffic from a Cisco IP Phone will be placed into VLAN 11.
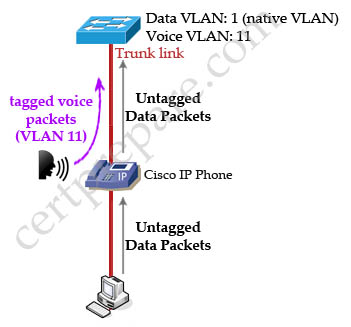
Note: In the above configuration, the data and voice use the same interface fa0/0 so it should be configured as a trunk link.
(Reference: http://www.cisco.com/en/US/products/hw/switches/ps4324/products_configuration_example09186a0080722cdb.shtml)
Question 10
Explanation
VLAN 1 is always used for CDP, VTP, PAgP traffic (except DTP uses native VLAN) even if VLAN 1 is not the native VLAN. If VLAN 1 is not the native VLAN then CDP, VTP, PAgP traffic will be tagged on the trunk.
In this question, after changing the default native VLAN to 999 while keeping the standard configuration on the other end, we cause a “native VLAN mismatched” error. Besides, CDP, VTP traffic is tagged on the local switch (as VLAN 1 is no longer the native VLAN) so the other end cannot understand them -> CDP, VTP traffic is dropped.
Question 11



Q10,
Tested on real gears,
Different encapsulation ISL/Dot1q causes the issue – not propagating vtp & cdp info
ANSWER IS BBBBBBBBBBB
Saji that is correct, different encapsulation definitely will cause the issue,
But as my understanding it is implied that it was working, then a network engineer JUST change Native vlan, then stop working.
So that my be tricky.