VLAN Hopping Questions
Here you will find answers to VLAN Hopping Questions
Question 1
What two steps can be taken to help prevent VLAN hopping? (Choose two)
A. Place unused ports in a common unrouted VLAN
B. Enable BPDU guard
C. Implement port security
D. Prevent automatic trunk configuration
E. Disable CDP on ports where it is not necessary
Answer: A D
Explanation
VLAN Hopping: By altering the VLAN ID on packets encapsulated for trunking, an attacking device can send or receive packets on
various VLANs, bypassing Layer 3 security measures. VLAN hopping can be accomplished by switch spoofing or double tagging.
1) Switch spoofing:

The attacker can connect an unauthorized Cisco switch to a Company switch port. The unauthorized switch can send DTP frames and form a trunk with the Company Switch. If the attacker can establish a trunk link to the Company switch, it receives traffic to all VLANs through the trunk because all VLANs are allowed on a trunk by default.
(Instead of using a Cisco Switch, the attacker can use a software to create and send DTP frames).
2) Double-Tagging:
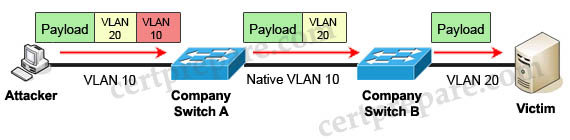
In this attack, the attacking computer generates frames with two 802.1Q tags. The first tag matches the native VLAN of the trunk port (VLAN 10 in this case), and the second matches the VLAN of a host it wants to attack (VLAN 20).
When the packet from the attacker reaches Switch A, Switch A only sees the first VLAN 10 and it matches with its native VLAN 10 so this VLAN tag is removed. Switch A forwards the frame out all links with the same native VLAN 10. Switch B receives the frame with an tag of VLAN 20 so it removes this tag and forwards out to the Victim computer.
Note: This attack only works if the trunk (between two switches) has the same native VLAN as the attacker.
Please notice that if the port in which the attacker connects to is an access port then he can make an attack too. But maybe you will wonder “what a switch do if it receives tagged traffic from an access port?”. Here is the answer quoted from Cisco site:
Traffic arriving on an access port is assumed to belong to the VLAN assigned to the port. If an access port receives a tagged packet (Inter-Switch Link [ISL] or 802.1Q tagged) for the VLAN assigned to the port, the packet is forwarded. If the port receives a tagged packet for another VLAN, the packet is dropped, the source address is not learned, and the frame is counted in the No destination statistic.
So in this case, the attacker is on VLAN 10, which is also the native VLAN -> the packet is forwarded.
To mitigate VLAN Hopping, the following things should be done:
1) If no trunking is required, configure port as an access port, this also disables trunking on that interface:
Switch(config-if)# switchport mode access
2) If trunking is required, try to configure the port to Nonegotiate to prevent DTP frames from being sent.
Switch(config-if)# switchport mode trunk
Switch(config-if)# switchport nonegotiate
-> Therefore answer D – Prevent automatic trunk configuration is correct.
3) Set the native VLAN to an unused VLAN and don’t use this VLAN for any other purpose:
Switch(config-if)# switchport trunk native vlan VLAN-ID
4) Force the switch to tag the native VLAN on all its 802.1Q trunks:
Switch(config)# vlan dot1q tag native
In this question, answer A – Place unused ports in a common unrouted VLAN is also correct because the Double-Tagging method requires the attacker’s port must be in the same VLAN with Native VLAN -> Place these ports in unrouted VLAN will put these ports in different VLAN from the Native VLAN.
Question 2
What is one method that can be used to prevent VLAN hopping on the network?
A. Configure VACLs.
B. Configure all frames with two 802.1Q headers.
C. Enforce username/password combinations.
D. Explicitly turn off Dynamic Trunking Protocol (DTP) on all unused ports.
E. All of the above
Answer: D
Explanation
Disable DTP so that switchport will not negotiate trunking on the link by this command:
| Switch(config-if)# switchport nonegotiate |
Or a better way is to configure it as an access port:
| Switch(config-if)# switchport mode access |
Note: VACLs should only be used to mitigate DHCP Snooping, not VLAN Hopping by filtering out DHCP Reply from outside ports.
Question 3
Which two statements about VLAN hopping are true? (Choose two)
A. Attacks are prevented by utilizing the port-security feature.
B. An end station attempts to gain access to all VLANs by transmitting Ethernet frames in the 802.1q encapsulation.
C. Configuring an interface with the “switchport mode dynamic” command will prevent VLAN hopping.
D. An end station attempts to redirect VLAN traffic by transmitting Ethernet frames in the 802.1q encapsulation.
E. Configuring an interface with the “switchport mode access” command will prevent VLAN hopping.
Answer: B E
Explanation
Please read the explanation of Question 1.
Question 4
When an attacker is using switch spoofing to perform VLAN hopping, how is the attacker able to gather information?
A. The attacking station uses DTP to negotiate trunking with a switch port and captures all traffic that is allowed on the trunk.
B. The attacking station tags itself with all usable VLANs to capture data that is passed through the switch, regardless of the VLAN to which the data belongs.
C. The attacking station will generate frames with two 802.1Q headers to cause the switch to forward the frames to a VLAN that would be inaccessible to the attacker through legitimate means.
D. The attacking station uses VTP to collect VLAN information that is sent out and then tags itself with the domain information in order to capture the data.
Answer: A
Explanation
Please read the explanation of Question 1.



hi