SDWAN Architecture Overview
SD-WAN represents the shift from an older, hardware-based model of legacy WAN to a secure, software-based, virtual IP fabric overlay that runs over standard network transport services. The Cisco SD-WAN solution is comprised of separate orchestration, management, control, and data planes:
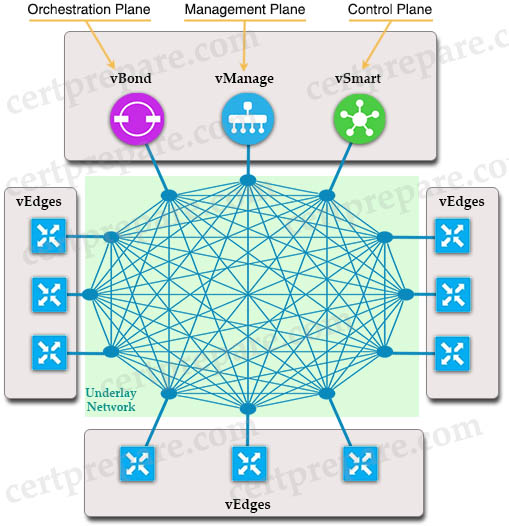
+ Orchestration plane (vBond) assists in securely onboarding the SD-WAN WAN Edge routers into the SD-WAN overlay. The vBond controller, or orchestrator, authenticates and authorizes the SD-WAN components onto the network. The vBond orchestrator takes an added responsibility to distribute the list of vSmart and vManage controller information to the WAN Edge routers. vBond is the only device in SD-WAN that requires a public IP address as it is the first point of contact and authentication for all SD-WAN components to join the SD-WAN fabric. All other components need to know the vBond IP or DNS information.
+ Management plane (vManage) is responsible for central configuration and monitoring. The vManage controller is the centralized network management system that provides a single pane of glass GUI interface to easily deploy, configure, monitor and troubleshoot all Cisco SD-WAN components in the network.
+ Control plane (vSmart) builds and maintains the network topology and make decisions on the traffic flows. The vSmart controller disseminates control plane information between WAN Edge devices, implements control plane policies and distributes data plane policies to network devices for enforcement.
+ Data plane (vEdge) is responsible for forwarding packets based on decisions from the control plane. WAN Edge physical or virtual devices provide secure data-plane connectivity between the sites in the same SD-WAN overlay network. WAN Edge devices are responsible for establishing secure connections for traffic forwarding, for security, encryption, Quality of Service (QoS) enforcement and more.
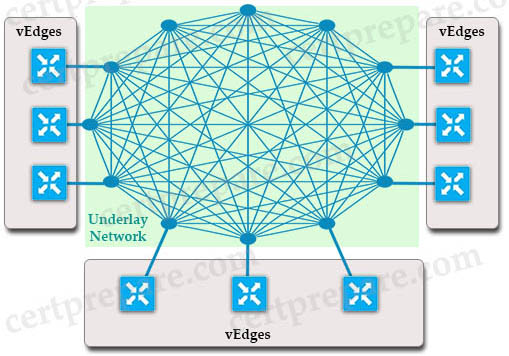
Data plane connections are only formed between vEdges. By default, vEdges will attempt to form an IPSec tunnel with every other vEdge across every link on each device. This kind of full mesh results in a lot of overhead just managing and maintaining IPSec. It is recommended to use policy to limit the topology to hub and spoke, partial mesh or something in between that makes sense to the business requirements.
In summary, the Cisco SD-WAN solution includes the vBond orchestrator on the orchestration layer, vManage on the management plane, vSmart controller on the control plane, and vEdge devices on the data plane. A summarization of the functions of each plane is shown below:
Orchestration Plane (Cisco vBond)
+ Orchestrates connectivity between management, control and data plane
+ First point of contact & authentication for all SD-WAN components to join the SD-WAN fabric
+ Requires dedicated public IP Address
+ Facilitates NAT traversal
+ All other components need to know the vBond IP or DNS information
+ Authorizes all control connections (white-list model)
+ Distributes list of vSmarts to all vEdges
Management Plane (Cisco vManage)
+ Intuitive GUI dashboard
+ Real time alerting
+ Centralized provisioning
+ Configuration standardization
+ Simplicity of deploying
+ Simplicity of change
+ Supports:
• REST API
• CLI
• Syslog
• SNMP
• NETCONF
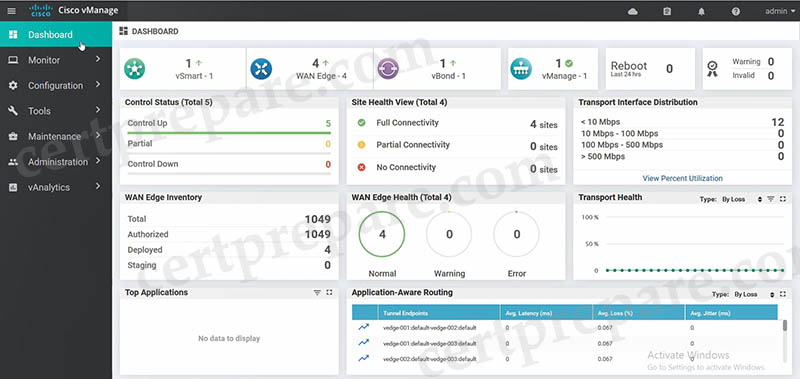 The vManage provides a single pane of glass GUI interface
The vManage provides a single pane of glass GUI interface
Control Plane (Cisco vSmart)
+ Centralized brain of the solution
+ Facilitates fabric discovery
+ Establishes OMP peering with all vEdges
+ Implements control plane policies, such as service chaining, traffic engineering and per VPN topology
+ Dramatically reduces complexity of the entire network
+ Distributes connectivity information between vEdge
+ Orchestrates secure data plane connectivity between vEdges
Data Plane (Physical/Virtual Cisco vEdge)
+ WAN edge router
+ Provides secure data plane with remote vEdge routers
+ Establishes secure control plane with vSmart controllers (OMP)
+ Implements data plane and application aware routing policies
+ Exports performance statistics
+ Leverages traditional routing protocols like OSPF, BGP and VRRP
+ Support Zero Touch Deployment
+ Physical or Virtual form factor (100Mb, 1Gb, 10Gb)
Underlay Network
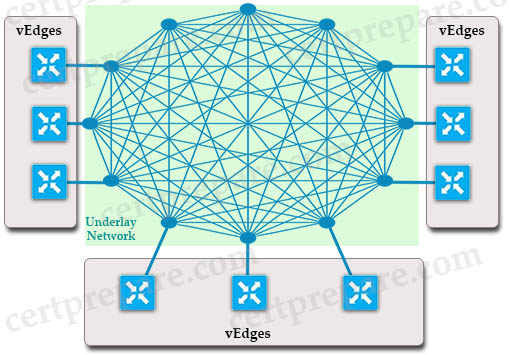
An underlay network is the underlying physical infrastructure of a network typically built from a number of routers and switches with a layer 3 routing protocol. In the topology above, underlay network is the full-mesh circle. It includes multiple WAN transport technologies such as MPLS, broadband, 4G, Internet connections…
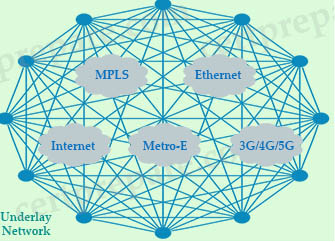
Overlay Network
The overlay network is a virtual IP fabric built on top of the underlay transport using IPsec tunnels. The fabric can be either full mesh, partial mesh or hub and spoke topologies.
Overlay network consists of:
+ The secure channels formed between the vEdges and the controllers (vBond, vManage, vSmart)
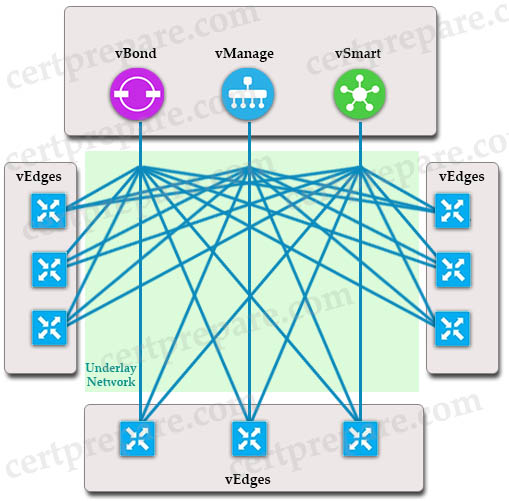
+ The secure channels formed between the vEdges:
Policies in SDWAN
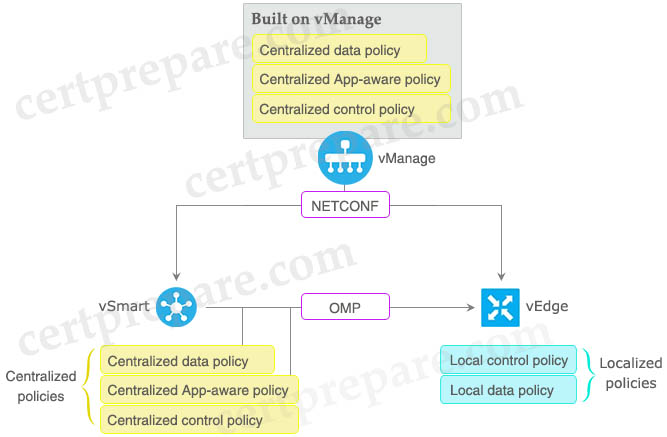
In traditional networking, policies are usually applied on each device manually using CLI. This leads to difficulty in code management. SD-WAN solves this problem by centralizing polices in vManage and vSmart devices.
Policies are created on vManage. When activated, they are pushed to vSmarts or to vEdges directly via NETCONF transactions.
There are two types of policy comprises:
+ Control (Routing) policy: which affects the flow of routing information in the network’s control plane. It is equivalent to routing protocol policy
+ Data policy: which affects the flow of data traffic in the network’s data plane. It is equivalent to access-list and firewall filters.
Both control policy and data policy comprise of centralized policy and localized policy.
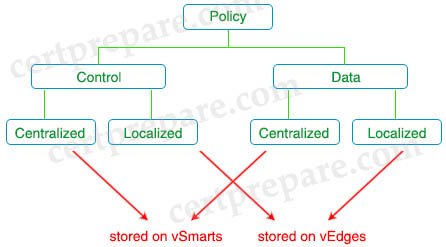
+ Centralized policy refers to policy built on vManage, provisioned and stored on vSmart. This policy is advertised to the vEdges so centralized control policy applies to the network-wide routing of traffic. Centralized policy affects the whole overlay fabric.
+ Localized policy refers to a policy that is provisioned locally through the CLI on the Cisco vEdge devices, or through a Cisco vManage device template. Localized policy only affects the local device (same as an access-list)
Besides two polices mentioned above, there is another type of policy: Application-Aware Policies. Application-Aware Policies can enforce/prevent application traffic of interest from being sent down the tunnels that do not satisfy the loss, latency or jitter SLA thresholds as defined by the administrator.
By default, no policy of any kind is configured on vEdge devices or vSmart devices.
In a centralized data policy, when a packet matches one of the match conditions, the associated action is taken and policy evaluation on that packet stops.
When configuring centralized policy in the vManage GUI, there are three main components:
Lists
Lists are used to group related items so you can reference them as a group. They are used when applying policy or used in matching or actions within the policy definitions. You can create lists for applications, color, data prefixes, policers, prefixes, sites, SLA classes, TLOCs, and VPNs. Data prefixes are used in data policies to define data prefixes, and prefixes are used in control polices to match on route prefixes.
Policy Definition
The policy definitions control the aspects of control and forwarding. Within the policy definition is where you create policy rules, specifying a series of match-action pairs which are examined in sequential order. There are several types of policy definitions: app-route policy, cflowd-template, control policy, data-policy, and a vpn-membership policy.
+ App-route Policy – Allows you to create an application-aware routing policy which tracks path characteristics such as loss,latency, and jitter. Traffic is put into different SLA categories (loss, delay, and jitter), and traffic is directed to different paths depending on the abilities to meet the SLA categories. In summary, traffic always transported across link that meet minimum SLA.
+ Cflowd Template – Allows you to enable cflowd, which sends sampled network data flows to collectors for analysis
+ Control Policy – Operates on the control plane traffic and influences the routing paths in the network
+ Data Policy – Influences the flow of data traffic based on the fields in the IP packet header
+ VPN Membership Policy – Can restrict participation in VPNs on vEdge routers and the population of their route tables.
Policy Application
The policy is applied to a site list.



I need your help Guys, could you please send me the questions with their answers for the ENSDWI exam
Hi ,any one have Latest dumps for 300-415 pls shared
is this updated?
Please update the certprepare for testing and learning purposes. Thanks in advance
Hi there
Anyone who have recently passed his/her CCNP SD-WAN Exam
Please comment with you advise to us who are preparing to take the exam soon!
Thank and looking forward to hear you
wrote the exam last week Friday, the exam is being updated again, 40% of questions came from here, 60% were completely new. But i passed anyway because i grasped the concept mostly.
@BP,tell me how many Questions you had,and how Many Labs you had,and Simulation Questions
how should I wait for the update?
how long
Anyone who has done the exam based on this current material? How is the experience? Feedback