VPNs in SD-WAN Tutorial
In the SD-WAN overlay, virtual private networks (VPNs) provide segmentation. Each VPN is equivalent to a VRF, which is isolated from one another and have their own forwarding tables. An interface or subinterface is explicitly configured under a single VPN and cannot be part of more than one VPN. Devices attached to an interface in one VPN cannot communicate with devices in another VPN unless policy is put in place to allow it. The VPN ranges from 0 to 65535, but several VPNs are reserved for internal use.
The Transport & Management VPNs
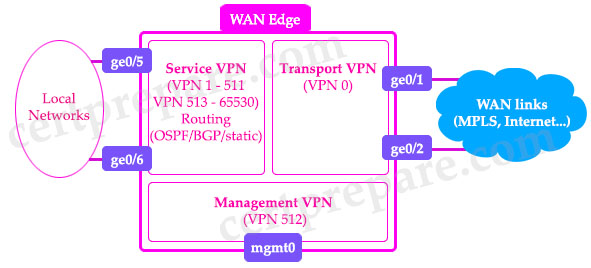
There are two implicitly configured VPNs in the WAN Edge devices and controllers: VPN 0 and VPN 512.
– VPN 0 is the transport VPN. It contains all the interfaces that connect to the (underlay) WAN links. Secure DTLS/TLS connections to the controllers are initiated from this VPN. Static or default routes or a dynamic routing protocol needs to be configured inside this VPN in order to get appropriate next-hop information so the control plane can be established and IPsec tunnel traffic can reach remote sites.
VPN 0 connects the WAN Edge to the WAN transport and creates control plane and data plane connections. The WAN Edge device can connect to multiple WAN transport(s) on different interfaces on the same VPN 0 transport segment. At least one interface needs to be configured to initially reach the SD-WAN controllers for onboarding.
– VPN 512 is the management VPN. It carries the out-of-band management traffic to and from the Cisco SD-WAN devices. This VPN is ignored by OMP and not carried across the overlay network.
VPN 0 and 512 are the only VPNs that can be configured on vManage and vSmart controllers. For the vBond orchestrator, although more VPNs can be configured, only VPN 0 and 512 are functional and the only ones that should be used.
Service VPNs
Service VPNs are defined as any VPN between 1 and 65530 (excluding 512). Interfaces associated with these VPNs are LAN facing. Our traditional routing protocols run in these VPNs. Each VPN can be thought of in the same way as a traditional VRF. Devices in a service VPN can only reach any other devices in the same VPN. Different service VPNs cannot communicate with each other without an explicit policy being defined to allow the communication. In summary, in WAN Edges VPN = VRF.
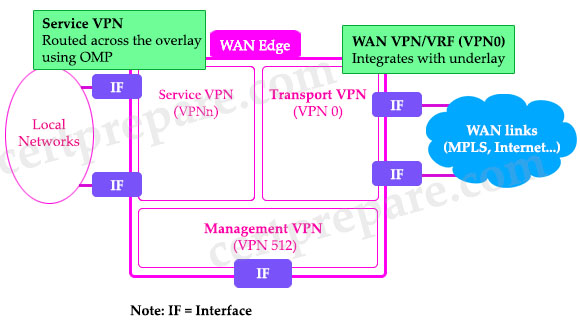
User traffic can be directed over the IPsec tunnels to other sites by redistributing OMP routes received from the vSmart controllers at the site into the service-side VPN routing protocol. In turn, routes from the local site can be advertised to other sites by advertising the service VPN routes into the OMP routing protocol, which is sent to the vSmart controllers and redistributed to the other WAN Edge routers in the network.
Note: In IOS XE SD-WAN routers, VRF is used instead of the VPN terminology.
Reference: https://www.cisco.com/c/en/us/td/docs/solutions/CVD/SDWAN/cisco-sdwan-design-guide.html



A amazing tutorial !!
This is by far the greatest and simplest explanation on VPNs in SDWAN i have ever came across..Bravo!1
Thank you. Clarified the confusion regarding difference between VPN and VRF.
Great Explanation ,Thank you .
1. What makes it vpn? Is it encrypted where ios xe vrf are not?
2. If using ios xe vrf for sd-wan, does “vrf 0” and “vrf 512” still function the same?
Where can I get premium subscription