Router Deployment
Question 1
Question 2
Question 3
Question 4
Explanation
Onboarding vEdge device using Zero-Touch-Provisioning
Step 1 – Connect the ZTP-supported vEdge device interface to the WAN transport (typically Internet).
Step 2 – Power on the vEdge router.
+ Upon bootup, the device dynamically obtains ip-address, default-gateway, and DNS information through the DHCP process from the upstream WAN transport device.
+ The vEdge device makes a DNS request to resolve ztp.viptela.com to the ZTP server.
+ The vEdge device reaches the ZTP server and presents its chassis and serial number in order to authenticate with the server.
+ Post authentication, the ZTP server provides information about the vBond orchestrator, organization-name and root certificates
Question 5
Explanation
By using “show bfd ?” command, we can see the “show bfd tloc-summary-list” displays the Per-TLOC BFD summary” information.
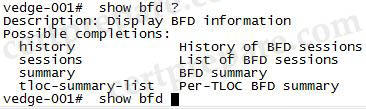
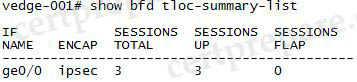
And the output of the “show bfd tloc-summary-list” command is shown below:
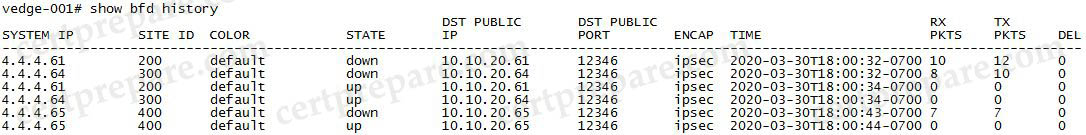
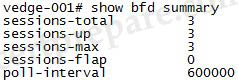
For your information, other “show bfd …” outputs are shown below:

Question 6
Explanation
The traffic flow of Direct Internet access (DIA) from a local Internet breakout is shown below:
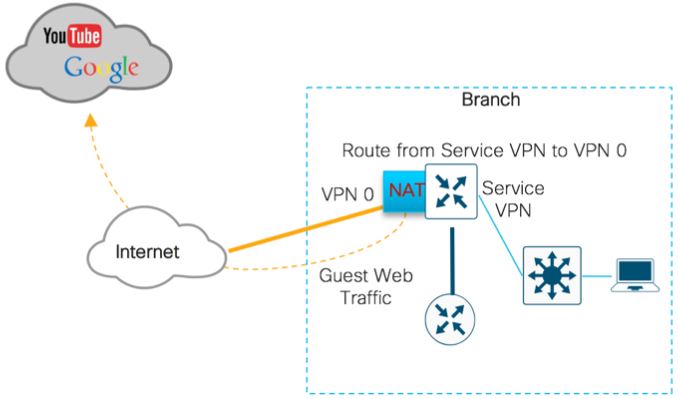
Design Considerations on using NAT DIA
Along with the configuration of a NAT DIA route within the service side VPN, ensure that you enable NAT on the Internet facing interface within VPN 0, as Internet traffic is redirected based on the NAT DIA route from the service-side to the NAT-enabled transport side interface.
Reference: https://www.cisco.com/c/dam/en/us/td/docs/solutions/CVD/SDWAN/sdwan-dia-deploy-2020aug.pdf
Therefore in order to configure DIA, we must:
+ Configure a NAT DIA route (via the command “ip route 0.0.0.0/0 vpn 0”) under a service VPN (VPN 10, for example)
+ Configure a NAT interface under VPN 0 for DIA.
-> Only answer A meets the requirements.
Question 7
Explanation
In the OMP feature template, the “Number of Paths Advertised per Prefix” and the ECMP Limit parameters will be changed from the default of four to the maximum number of 16.
The “Number of paths advertised per prefix” specifies the maximum number of equal-cost routes to advertise per prefix.
The picture in answer B is Logging feature template (with source logging interface is Loopback0) while in answer C is AAA feature template. The picture in answer D is VPN 512 feature template (out-of-band management VPN and this VPN cannot be used for any other purpose).
If you wonder why we see the “Radio button” type in VPN 512 feature template then this picture will explain:
Question 8
Explanation
From the exhibit above we can draw the topology of this question as follows:
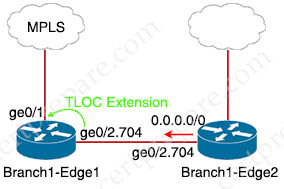 With above configuration, only Branch1-Edge2 router sends traffic to Branch1-Edge1 router if the main route to MPLS fails (as only Edge2 has the default route to Edge1). Therefore we have to configure the TLOC Extension under subinterface ge0/2.704 of Branch1-Edge1 with the command “tloc-extension ge0/1”.
With above configuration, only Branch1-Edge2 router sends traffic to Branch1-Edge1 router if the main route to MPLS fails (as only Edge2 has the default route to Edge1). Therefore we have to configure the TLOC Extension under subinterface ge0/2.704 of Branch1-Edge1 with the command “tloc-extension ge0/1”.
Note: We change the mtu to 1496 to accommodate for the dot1q tag.
Question 9
Explanation
We can check the function of these commands with the “show omp ?” command:
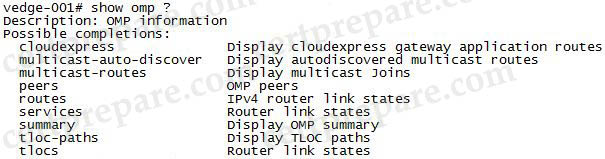
Only the “show omp tlocs” command displays the “COLOR”:
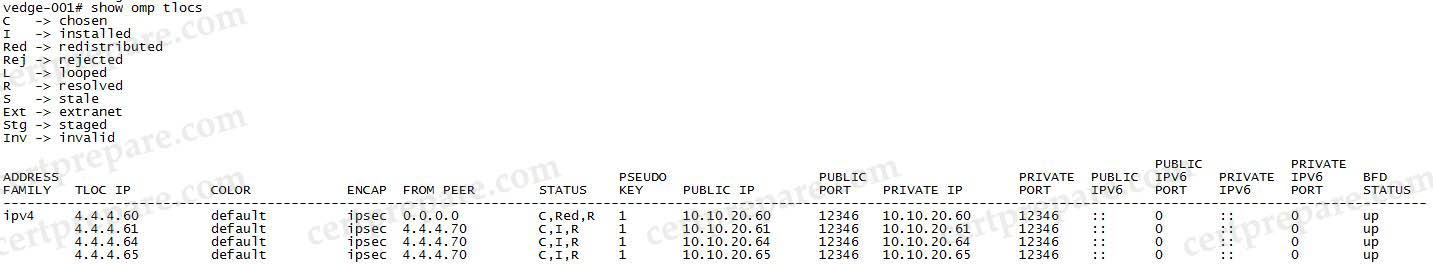
Question 10
Explanation
This is an unclear question because VRRPv3 supports both IPv4 and IPv6. VRRP also support encrypted authentication (MD5) so maybe this question was asked based on the paragraph below:
VRRP Limitations
+ You can configure both HSRP and VRRP on a switch or switch stack. However, you cannot add a switch model that supports only one protocol to a stack that is configured for both protocols.
+ The VRRP implementation on the switch does not support the MIB specified in RFC 2787.
+ The VRRP implementation on the switch supports only text -based authentication.
+ The switch supports VRRP only for IPv4.



Q10 wrong.
correct=C
Which statement about VRRP is true?
A. It supports load balancing
B. It can be configured with HSRP on a switch or switch stack
C. It supports IPv4 and IPv6
D. It supports encrypted authentication
Answer: ACD
q.10 correct answer is C
VRRP support encrypted authentication. load balancing and ipv4 and ipv6
Q3,
C. Set OMP admin distance lower than BGP admin distance
https://www.cisco.com/c/dam/en/us/td/docs/routers/sdwan/migration-guide/cisco-sd-wan-migration-guide.pdf
Since there are typically two edge routers at the datacenter and both devices perform
redistribution between OMP and LAN routing protocol, there can be a routing loop. Make
sure that prefixes learned from an SD-WAN site are not redistributed into OMP again at the
datacenter, which can allow loops. If BGP is the datacenter LAN protocol, then configure
both edge routers in the same autonomous system (AS) and create eBGP neighborhood
between the core routers and edge routers. Because of the same BGP AS-PATH, the second
edge router will not install any of the routes that were originally redistributed by the other
edge router from OMP.
@Anonymous Then the answer is D. Set same overlay AS on both DC WAN Edge routers
You CAN’T change the admin distance for OMP.
Which configuration step is taken on vManage after WAN Edge list is uploaded to support the on-boarding process before the device comes online?
A. Verify the device certificate
B. Enable the ZTP process
C. Set the device as valid
D. Send the list to controllers
Answer: C
Correct answer is D, the devices are valid by default. You can set them to stage or invalidated them at a later time, but by default they are valid!
Correction, C is the correct answer. If you check the box for :”Validate the uploaded vEdge list and send to controllers” then they are validated but also sent to controllers.
Q6 I am guessing the question. For DIA you need 2 essential components, one is NAT on VPN0 and the other is a route to VPN0. Without NAT on VPN0 your trying to expose your internal IP addressing to the internet. Suggest rather than just the default route deciding the answer you look for the answer that has both NAT and the route.
Refer.
https://sdwan-docs.cisco.com/Product_Documentation/Software_Features/SD-WAN_Release_16.3/07Policy_Applications/04Using_a_vEdge_Router_as_a_NAT_Device/Configuring_Local_Internet_Exit
Could you verify question 6 …. In my opinion the correct answer is B ….
Q6, option C seems to be completely incorrect to myself as it states to drop You Tube traffic rather than accepting it. Option D provides just a route to VPN 0. I agree with @magdccsar that the policy that accepts You Tube is B. Which appears to be the correct response.
If the answer is C can some one explain how dropping You Tube permits that traffic to be passed?
Thanks
Q3 when used in compsite quiz has incorrect answer of C which conflicts with the states correct answer.
@maybe: Thanks for your detection, we have just updated Q3.
@certprepare Could you verify question Q6?
@magdccsar: Thanks for your information, Q.6 answer should be A. We have just updated it!
@Certprepare great that you updated the response to Q6. Prior to posting earlier I had tested and validated the configuration in the lab. All other options other than A only provide a potential for the service side (or NAT inside) interface. Only option A provides the NAT outside and inside option.
so the correct answer for Q 8 is D?
I don’t think answer for Q10 is B. The reference document is for ancient IOS. Current VRRP supports both IPv4 and IPv6, so I think correct answer is C.
Q10 is correct. I have a lab set up and in case of vEdge VRRP does not support ipv6 and encrypted authentication, nor load balancing because VRRP is always active/standby.
vEdge4(config-interface-ge0/2)# vrrp ?
Possible completions:
vEdge4(config-interface-ge0/2)# vrrp 1 ?
Possible completions:
ipv4 Assign IP address
priority Set priority
timer Timer interval for successive advertisements, in seconds
track-omp Track OMP status
track-prefix-list Track Prefix list
-A
@certprepare Can you confirm that the option A (setting the internet facing interface as Nat) is the correct answer? I was thinking using a data policy would be more appropriate given the fact that the question asked that traffic from youtube specifically be able to do a Direct internet breakout
@certprepare: Is there any new questions after September 10th, 2020 ?
why there are no questions?
Anyone passed the exam recently?