DHCP Snooping 2
Question 1
Explanation
The DHCP snooping database stores at least 8,000 bindings.
Question 2
Explanation
IP Source Guard is a security feature that restricts IP traffic on untrusted Layer 2 ports by filtering traffic based on the DHCP snooping binding database or manually configured IP source bindings
Initially, all IP traffic on the protected port is blocked except for DHCP packets. After a client receives an IP address from the DHCP server, or after static IP source binding is configured by the administrator, all traffic with that IP source address is permitted from that client. Traffic from other hosts is denied. This filtering limits a host’s ability to attack the network by claiming a neighbor host’s IP address.
Before enabling IP Source Guard, DHCP Snooping must be enabled as a prerequisite. Let’s see an example of how to configure IP Source Guard.
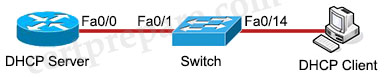
Enable DHCP Snooping first:
| Switch(config)#ip dhcp snooping Switch(config)#ip dhcp snooping vlan 1 Switch(config)#int fa0/1 Switch(config-if)#ip dhcp snooping trust Switch(config)#int fa0/14 Switch(config-if)#ip dhcp snooping limit rate 20 |
Next we can start configuring IP Source Guard.
| Switch(config)#int fa0/14 Switch(config-if)#ip verify source |
IP Source Guard is configured at the access layer (in this case under interface Fa0/14) and uses the DHCP Snooping database, or static IP binding entries, to dynamically create ACLs on a per-port basis. Any traffic which doesn’t match the binding entries is dropped in hardware.
If we want to enable IP source guard with source IP and MAC address filtering, use the command “ip verify source port-security” instead (Port security and option 82 is not necessary if you are not using MAC verification).
Well now maybe you understand about IP source guard. Let’s learn about option 82.
When a client initially connects to a port protected by IP source guard (Fa0/14 of the switch in the above case) only DHCP discover and request messages are allowed, everything else is dropped. An important point to keep in mind is that at this point no traffic, including DHCP, will cause the switch to add an entry for the client in the CAM table and therefore when the DHCP server responds with an offer the switch will not know where to send the packet. And when DHCP snooping is enabled, replies from the DHCP server are not flooded out all ports if there is no entry in the CAM, so the DHCP offer will be dropped. To get around this, DHCP option 82 (or Relay Agent Information) is necessary. Option 82 is a frequently misunderstood value, likely because unlike other options it is not set by the DHCP server, rather it is set by an intermediary device such as a DHCP relay agent or a switch. Option 82 is made up of two fields, the circuit ID and remote ID.
When a DHCP packet is received on an untrusted port the switch adds the option 82 information and sends it on it’s way, if the option 82 field already exists the packet will be dropped (this behavior can be changed by using the ‘ip dhcp snooping information option allow-untrusted’ command under interface configuration). When the DHCP server receives the discover it is expected to return the values in option 82 with it’s offer. Assuming that the server does support option 82 and returns an offer with the information intact, the switch will determine whether it is the originator of the option 82 information by checking whether the MAC address in the remote ID field matches it’s own, it then looks at the VLAN, module, and port carried in the circuit ID field to find out which port the packet should be sent out, the switch then strips option 82 out of the packet and forwards it to the specified port. The same process will occur with the request and ack portion of DHCP. If the offer is sent back from the DHCP server without the option 82 information the switch is unable to determine where the packet should be sent and drops it.
Reference: http://vcabbage.com/networking/2010/08/07/ip-source-guard.html
Question 3
Question 4
Explanation
DHCP snooping is a security feature that acts like a firewall between untrusted hosts and trusted DHCP servers. The DHCP snooping feature performs the following activities:
+ Validates DHCP messages received from untrusted sources and filters out invalid messages.
+ Rate-limits DHCP traffic from trusted and untrusted sources.
+ Builds and maintains the DHCP snooping binding database, which contains information about untrusted hosts with leased IP addresses.
+ Utilizes the DHCP snooping binding database to validate subsequent requests from untrusted hosts.
Reference: https://www.cisco.com/en/US/docs/general/Test/dwerblo/broken_guide/snoodhcp.html
Question 5
Explanation
To configure DHCP snooping feature, at least three steps must be done:
| Sequence and Description | Command |
| 1. Configure global DHCP snooping | Switch(config)# ip dhcp snooping |
| 2. Configure trusted ports (as least on 1 port). By default, all ports are untrusted |
Switch(config-if)# ip dhcp snooping trust |
| 3. Configure DHCP snooping for the selected VLANs | Switch(config)# ip dhcp snooping vlan {VLAN-ID | VLAN range} |
Other steps are just optional:
+ Configure DHCP Option 82
Switch(config)# ip dhcp snooping information option
+ Configure the number of DHCP packets per second (pps) that are acceptable on the port:
Switch(config-if)# ip dhcp snooping limit rate {rate}
Reference: SWITCH Student Guide
Note: To configure DHCP snooping with Dynamic ARP Inspection we need to add the command “ip arp inspection vlan vlan-id” in global configuration mode and “ip arp inspection trust” in interface mode.
Question 6
Explanation
The DHCP snooping feature updates the database when the switch receives specific DHCP messages. For example, the feature adds an entry to the database when the switch receives a DHCPACK message from the server.
Question 7
Question 8
Question 9
Explanation
DHCP snooping is a security feature that acts like a firewall between untrusted hosts and trusted DHCP servers. The DHCP snooping feature performs the following activities:
+ Validates DHCP messages received from untrusted sources and filters out invalid messages.
+ Rate-limits DHCP traffic from trusted and untrusted sources.
+ Builds and maintains the DHCP snooping binding database, which contains information about untrusted hosts with leased IP addresses.
+ Utilizes the DHCP snooping binding database to validate subsequent requests from untrusted hosts.
Reference: https://www.cisco.com/en/US/docs/general/Test/dwerblo/broken_guide/snoodhcp.html
Note: In fact this question is same as Question 14 of https://www.certprepare.com/dhcp-snooping
Question 10
Explanation
Note: To configure DHCP snooping with Dynamic ARP Inspection we need to add the command “ip arp inspection vlan vlan-id” in global configuration mode and “ip arp inspection trust” in interface mode.


