Port Security Questions
Here you will find answers to Port Security Questions
Quick review:
Port security feature can be used to limit the number of MAC addresses on a port. It can also allow specific MAC addresses to send traffic into that port.
Question 1
Which of the following should you enable to prevent a switch from forwarding packets with source addresses that are outside an administratively defined group? (Select the best answer)
A. DAI
B. STP
C. PVLAN
D. port security
Answer: D
Explanation
When you assign secure MAC addresses to a secure port, the port does not forward ingress traffic that has source addresses outside the group of defined addresses.
The example below configures secure MAC address 0000.1234.5678. Only traffic from this MAC is forwarded.
Switch(config)# interface fastethernet 0/1
Switch(config-if)# switchport mode access
Switch(config-if)# switchport port-security
Switch(config-if)# switchport port-security mac-address 0000.1234.5678
(Reference: http://www.cisco.com/en/US/docs/switches/lan/catalyst6500/ios/12.2SX/configuration/guide/port_sec.html)
Question 2
You need to configure port security on switch R1. Which two statements are true about this technology? (Choose two)
A. Port security can be configured for ports supporting VoIP.
B. With port security configured, four MAC addresses are allowed by default.
C. The network administrator must manually enter the MAC address for each device in order for the switch to allow connectivity.
D. With port security configured, only one MAC addresses is allowed by default.
E. Port security cannot be configured for ports supporting VoIP.
Answer: A D
Explanation
Port security can be set on ports supporting VoIP. This example shows how to designate a maximum of one MAC address for a voice VLAN (for a Cisco IP Phone) and one MAC address for the data VLAN (for a PC) on Fast Ethernet interface 5/1 and to verify the configuration:
Switch(config)# interface fa5/1
Switch(config-if)# switchport mode access
Switch(config-if)# switchport port-security
Switch(config-if)# switchport port-security mac-address sticky
Switch(config-if)# switchport port-security maximum 1 vlan voice
Switch(config-if)# switchport port-security maximum 1 vlan access
-> A is correct.
By default, only one MAC addresses is allowed but we can use the “switchport port-security maximum number” command to set the maximum number of MAC allowed -> D is correct.
(Reference: http://www.cisco.com/en/US/docs/switches/lan/catalyst4500/12.2/31sg/configuration/guide/port_sec.html)
Question 3
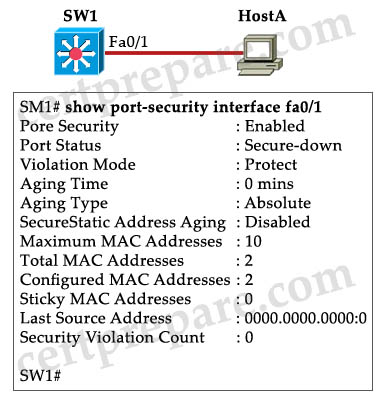
Refer to the exhibit. The “show port-security interface fa0/1” command was issued on switch SW1. Given the output that was generated, which two security statements are true? (Choose two)
A. Interface FastEthernet 0/1 was configured with the switchport port-security aging command.
B. Interface FastEthernet 0/1 was configured with the switchport port-security violation protect command.
C. Interface FastEthernet 0/1 was configured with the switchport port-security violation restrict command.
D. When the number of secure IP addresses reaches 10, the interface will immediately shut down.
E. When the number of secure MAC addresses reaches 10, the interface will immediately shut down and an SNMP trap notification will be sent.
Answer: B E (wrong)
Explanation
The “Violation Mode: Protect” tells us this interface has been configured with the switchport port-security violation protect command. Protect mode drops packets with unknown source addresses when the violation occurs -> B is correct.
Well, I cannot say answer E is correct. There is something wrong here. In “Protect” mode, when the number of secure MAC addresses reaches 10, the interface will not be shut down (it just drops unknown source MAC); also an SNMP trap notification will not be sent (an SNMP would be sent in “Shutdown” or “Restrict” mode). So in the exam you I am sure you will see another version of answer E.
Question 4
Refer to the exhibit. Which interface or interfaces on switch SW_A can have the port security feature enabled?
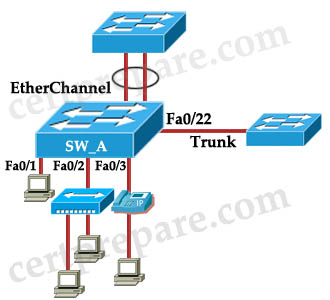
A. Ports 0/1 and 0/2
B. The trunk port 0/22 and the EtherChannel ports
C. Ports 0/1, 0/2 and 0/3
D. Ports 0/1, 0/2, 0/3, the trunk port 0/22 and the EtherChannel ports
E. Port 0/1
F. Ports 0/1, 0/2, 0/3 and the trunk port 0/22
Answer: C
Explanation
Port security can only be configured on static access ports or static trunk ports (DTP disabled). In this case we don’t know if the ports of the trunk link have DTP disabled or not -> only Fa0/1, Fa0/2 and Fa0/3 can be configured port security.
Question 5
When configuring port security on a Cisco Catalyst switch port, what is the default action taken by the switch if a violation occurs?
A. protect (drop packets with unknown source addresses)
B. restrict (increment SecurityViolation counter)
C. shutdown (access or trunk port)
D. transition (the access port to a trunking port)
Answer: C
Explanation
There are three port security violation modes:
+ protect – Drops packets with unknown source addresses until you remove a sufficient number of secure MAC addresses to drop below the maximum value.
+ restrict – Drops packets with unknown source addresses until you remove a sufficient number of secure MAC addresses to drop below the maximum value and causes the SecurityViolation counter to increment.
+ shutdown – Puts the interface into the error-disabled state immediately and sends an SNMP trap notification.
The default behavior for a security violation is to shut down that port permanently.
(Reference: http://www.cisco.com/en/US/docs/switches/lan/catalyst6500/ios/12.2SX/configuration/guide/port_sec.html)
Question 6
You are responsible for increasing the security within the Company LAN. Of the following choices listed below, which is true regarding layer 2 security and mitigation techniques?
A. Enable root guard to mitigate ARP address spoofing attacks.
B. Configure DHCP spoofing to mitigate ARP address spoofing attacks.
C. Configure PVLANs to mitigate MAC address flooding attacks.
D. Enable root guard to mitigate DHCP spoofing attacks.
E. Configure dynamic APR inspection (DAI) to mitigate IP address spoofing on DHCP untrusted ports.
F. Configure port security to mitigate MAC address flooding.
Answer: F
Explanation
Root guard is used to mitigate Spanning-tree compromises, not ARP address spoofing -> A and D are not correct.
DHCP spoofing is mitigated by DHCP snooping -> B is not correct.
PVLAN is often used to protect devices on a common VLAN, give them more separation even though they are on the same VLAN. It is not used to mitigate MAC address flooding attacks -> C is not correct.
DAI should be used to mitigate ARP Spoofing attack in which the attacker fakes its MAC as the destination MAC to receive traffic intended for valid destination -> E is not correct.
MAC flooding attack is a technique in which the attacker floods the switch with packets, each containing different source MAC address. This makes the switch learn the MAC addresses until its memory is used up. Now the switch acts like a hub, in which all incoming packets are broadcast out on all ports instead of just to the correct destination port as normal operation. The attacker can listen to these broadcast packets and capture sensitive data.
To protect against this type of attack, port security feature can be used to limit and allow specific MAC to access the port -> F is correct. (VLAN Access map with a “mac access list” can also be used to filter MAC).
Question 7
Refer to the exhibit. From the configuration shown, what can be determined?
| Switch(config)# interface FastEthemet0/1 Switch(config-if)# switchport access vlan 21 Switch(config-if)# switchport mode access Switch(config-if)# switchport voice vlan 22 Switch(config-if)# switchport port-security Switch(config-if)# switchport port-security maximum 20 Switch(config-if)# switchport port-security violation restrict Switch(config-if)# switchport port-security mac-address sticky Switch(config-if)# switchport port-security mac-address sticky 0000.0000.0002 Switch(config-if)# switchport port-security mac-address 0000.0000.0003 Switch(config-if)# switchport port-security mac-address sticky 0000.0000.0001 vlan voice Switch(config-if)# switchport port-security mac-address 0000.0000.0004 vlan voice Switch(config-if)# switchport port-security maximum 10 vlan access Switch(config-if)# switchport port-security maximum 10 vlan voice |
A. The sticky addresses will only be those manually configured MAC addresses enabled with the sticky keyword.
B. The remaining secure MAC addresses will be dynamically learned, converted to sticky secure MAC addresses, and added to the running configuration.
C. Since a voice VLAN is configured in this example, port security should be set for a maximum of 2.
D. A security violation will restrict the number of addresses to a maximum of 10 addresses per access VLAN and voice VLAN. The port will be shut down if more than 10 devices per VLAN attempt to access the port.
Answer: B
Explanation
The “sticky” keyword in switchport port-security mac-address sticky command converts all the dynamic secure MAC addresses, including those that were dynamically learned before sticky learning was enabled, to sticky secure MAC addresses and adds to the running configuration.
Question 8
What are two methods of mitigating MAC address flooding attacks? (Choose two)
A. Place unused ports in a common VLAN.
B. Implement private VLANs.
C. Implement DHCP snooping.
D. Implement port security.
E. Implement VLAN access maps.
Answer: D E
Explanation
MAC flooding attack is a technique in which the attacker floods the switch with packets, each containing different source MAC address. This makes the switch learn the MAC addresses until its memory is used up. Now the switch acts like a hub, in which all incoming packets are broadcast out on all ports instead of just to the correct destination port as normal operation. The attacker can listen to these broadcast packets and capture sensitive data.
To protect against this type of attack, port security feature can be used to limit and allow specific MAC to access the port. VLAN Access map with a “mac access list” can also be used to filter MAC -> D & E are correct.
Question 9
Given the configuration on a switch interface, what happens when a host with the MAC address of 0003.0003.0003 is directly connected to the switch port?
| switchport mode access switchport port-security switchport port-security maximum 2 switchport port-security mac-address 0002.0002.0002 switchport port-security violation shutdown |
A. The host will be allowed to connect.
B. The port will shut down.
C. The host can only connect through a hub/switch where 0002.0002.0002 is already connected.
D. The host will be refused access.
Answer: A
Explanation
The maximum number of hosts allowed to connect is set to 2. One of them is specified as MAC 0002.0002.0002 so another MAC can be allowed to connect.
Question 10
Refer to the exhibit. Which of these is true based upon the output shown in the command?
| switch# show port-security interface fastethernet 0/1 Port Security: Enabled Port status: SecureUp Violation mode: Shutdown Maximum MAC Addresses: 11 Total MAC Addresses: 11 Configured MAC Addresses: 3 Aging time: 20 mins Aging type: Inactivity SecureStatic address aging: Enabled Security Violation count: 0 |
A. If the number of devices attempting to access the port exceeds 11, the port will shut down for 20 minutes, as configured.
B. The port has security enabled and has shut down due to a security violation.
C. The port is operational and has reached its configured maximum allowed number of MAC addresses.
D. The port will allow access for 11 MAC addresses in addition to the 3 configured MAC addresses.
Answer: C
Explanation
Notice that the “Violation mode: Shutdown” line only describes what the switch will do if a violation occurs; it is not the current status of that port. The last line “Security Violation count: 0” tells us no violation has occurred -> the port is operational. Also “the Maximum MAC” and “Total MAC Addresses” are both 11 -> the maximum MAC addresses have ben reached.
From the “Configured MAC Addresses: 3” we also learn that there are 3 MAC addresses are manually learned and 8 MAC addresses are dynamically learned.


