DHCP Snooping
|
Quick review of DHCP Spoofing:
DHCP spoofing is a type of attack in that the attacker listens for DHCP Requests from clients and answers them with fake DHCP Response before the authorized DHCP Response comes to the clients. The fake DHCP Response often gives its IP address as the client default gateway -> all the traffic sent from the client will go through the attacker computer, the attacker becomes a “man-in-the-middle”. The attacker can have some ways to make sure its fake DHCP Response arrives first. In fact, if the attacker is “closer” than the DHCP Server then he doesn’t need to do anything. Or he can DoS the DHCP Server so that it can’t send the DHCP Response. DHCP snooping can prevent DHCP spoofing attacks. DHCP snooping is a Cisco Catalyst feature that determines which switch ports can respond to DHCP requests. Ports are identified as trusted and untrusted.
Only ports that connect to an authorized DHCP server are trusted, and allowed to send all types of DHCP messages. All other ports on the switch are untrusted and can send only DHCP requests. If a DHCP response is seen on an untrusted port, the port is shut down. |
Question 1
Explanation
To retain the bindings across switch reloads, you must use the DHCP snooping database agent. Without this agent, the bindings established by DHCP snooping are lost upon switch reload. Connectivity is lost as well.
Question 2
Explanation
Static DHCP snooping binding defines a mapping between a fixed IP address and the client’s MAC address. Each entry in the DHCP snooping binding database includes the MAC address of the host, the leased IP address, the lease time, the binding type, and the VLAN number and interface information associated with the host. This is how to configure a static DHCP snooping binding entry:
| Switch#ip dhcp snooping binding mac-address vlan vlan-id ip-address interface interface expiry seconds |
Question 3
Explanation
IP Source Guard provides source IP address filtering on a Layer 2 port to prevent a malicious host from impersonating a legitimate host by assuming the legitimate host’s IP address. The feature uses dynamic DHCP snooping and static IP source binding to match IP addresses to hosts on untrusted Layer 2 access ports.
Initially, all IP traffic on the protected port is blocked except for DHCP packets. After a client receives an IP address from the DHCP server, or after static IP source binding is configured by the administrator, all traffic with that IP source address is permitted from that client. Traffic from other hosts is denied. This filtering limits a host’s ability to attack the network by claiming a neighbor host’s IP address.
Therefore if the switch receives a packet that does not match any entries found in the DHCP binding database, that packet is assumed to be spoofed and will be discarded.
Question 4
Explanation
The command “ip verify source port-security” enables IP source guard with source IP and MAC address filtering. When using this command, there are two caveats:
+ The DHCP server must support option 82, or the client is not assigned an IP address.
+ The MAC address in the DHCP packet is not learned as a secure address. The MAC address of the DHCP client is learned as a secure address only when the switch receives non-DHCP data traffic.
Question 5
Explanation
The following restrictions apply to IP source guard:
+ Supported only on ingress Layer 2 ports (including access and trunk ports)
+ Supported only in hardware; not applied to any traffic that is processed in software.
+ Does not support filtering of traffic based on MAC address.
+ Is not supported on private VLANs.
Question 6
Explanation
The DHCP snooping binding database contains information about untrusted hosts with leased IP addresses. Each entry in the DHCP snooping binding database includes the MAC address of the host, the leased IP address, the lease time, the binding type, the VLAN number and interface information associated with the host.
Question 7
Explanation
The port connected to a DHCP server should be configured as trusted port with the “ip dhcp snooping trust” command. Other ports connecting to hosts are untrusted ports by default.
Question 8
Explanation
DHCP snooping database contains MAC address-to-IP address bindings which Dynamic ARP Inspection (DAI) uses to determine the validity of an ARP packet.
Question 9
Explanation
When IP Source Guard with source IP filtering is enabled on an untrusted interface, DHCP snooping must be enabled because it filters traffic based on IP information stored in the corresponding DHCP binding table entry.
Question 10
Explanation
The function of DAI is:
+ Intercepts all ARP requests and responses on untrusted ports
+ Verifies that each of these intercepted packets has a valid IP-to-MAC address binding before updating the local ARP cache or before forwarding the packet to the appropriate destination
+ Drops invalid ARP packets
On untrusted ports, the switch captures all ARP packets (both request and reply) and then validates the Source Protocol and Source Hardware address values against the snooping table database for that port.
If the MAC address and IP address and the corresponding port do not match the snooping database entry, the ARP packets are dropped. DAI thus prevents the node from specifying a non-legitimate IP-MAC address binding which differs from what was given by the DHCP server.


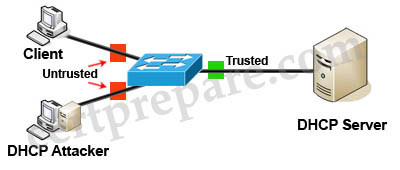


Question 31:
Which type of packet does DHCP snooping continuously check in a production network?
A. DHCP Snooping
B. DHCP Relay
C. DHCP Request
D. DHCP Acknowledge
E. DHCP Reply
F. DHCP Allow
There are only two options that are talked about concerning DHCP snooping operation. Of those options, Request and ACK are listed.
This quote from page 451 of the OFFICIAL GUIDE “”””Any DHCP REPLIES coming from an untrusted port are discarded because they must have come from a rogue DHCP server”””
^This isn’t talking about replies as in REPLIES being an option in the packet. It is just saying that DHCP replies coming from an untrusted port…etc, etc, etc. Replies isn’t an actual option inside any packets. “replies” is being used as basic conversational writing in this quote.
Client messages coming in on untrusted ports contain these:
(Discover, Request/Inform, Decline, Release).
Server messages coming from untrusted ports contain these:
(Offer, ACK, NACK, Leasequery).
These are the only ones of that choice list for the question that should be looked at. Of that list, ACK and Request are the only ones available to choose from.
Q2: the answer is C
You only create snooping binding to leased addresses, lease time (expiry) is required.
Eventhough I’ve passed switch, and route, I will continue to say that Cisco exams are terrible tests made to cheat people out of their money.
I remember having a question that read “what are the minimum binding addresses in a binding table”. This was in September.
1000
2000
5000
8000
12000
Literally this could vary depending on the IOS. This is an example of garbage.
And why are my post being deleted? Everytime I post something exposing Cisco, the post is missing after 2-3 days.