Port Security Questions 2
Here you will find answers to Port Security Questions – Part 2
Question 1
Refer to the exhibit. Based on the running configuration that is shown for interface FastEthemet0/2, what two conclusions can be deduced? (Choose two)
| ! interface FastEthernet0/2 switchport mode access switchport port-security switchport port-security maximum 6 switchport port-security aging time 5 switchport port-security aging static switchport port-security mac-address sticky switchport port-security mac-address 0000.0000.000b switchport port-security mac-address sticky 0000.0000.4141 switchport port-security mac-address sticky 0000.0000.5050 no ip address |
A. Connecting a host with MAC address 0000.0000.4147 will move interface FastEthemet0/2 into error disabled state.
B. The host with address 0000.0000.4141 is removed from the secure address list after 5 seconds of inactivity.
C. The sticky secure MAC addresses are treated as static secure MAC addresses after the running configuration is saved to the startup configuration and the switch is restarted.
D. Interface FastEthemet0/2 is a voice VLAN port.
E. The host with address 0000.0000.000b is removed from the secure address list after 300 seconds.
Answer: C E
Explanation
In this case the “switchport port-security aging time 5” sets aging time to 5 minutes and the “switchport port-security aging static” tells the switch to age out for statically configured MAC addresses -> the MAC 0000.0000.000b will be aged out after 5 minutes (300 seconds).
Note: Cisco switch does not support port security aging of sticky secure MAC addresses -> the sticky secure MAC addresses are not aged out.
Question 2
Refer to the exhibit. What will happen when one more user is connected to interface FastEthernet 5/1?
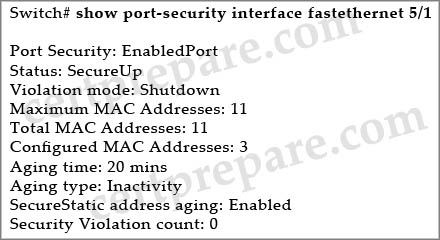
A. The first address learned on the port will be removed from the secure address list and be replaced with the new address.
B. All secure addresses will age out and be removed from the secure address list. This will cause the security violation counter to increment.
C. The packets with the new source addresses will be dropped until a sufficient number of secure MAC addresses are removed from the secure address list.
D. The interface will be placed into the error-disabled state immediately, and an SNMP trap notification will be sent.
Answer: D
Explanation
There are three violation mode of port security:
+ Protect: drop packets (port is not shutdown)
+ Restrict: drop packets and increase violation counter, send SNMP trap notification (port is not shutdown)
+ Shutdown (default mode): put port into error-distabled state (same as shutdown state), send SNMP trap notification
Question 3
When you enable port security on an interface that is also configured with a voice VLAN, what is the maximum number of secure MAC addresses that should be set on the port?
A. No more than one secure MAC address should be set.
B. The default will be set.
C. The IP phone should use a dedicated port, therefore only one MAC address is needed per port.
D. No value is needed if the switchport priority extend command is configured.
E. No more than two secure MAC addresses should be set.
Answer: E
Explanation
Usually, an IP Phone needs two MAC addresses, one for the voice vlan and one for the access vlan. If you don’t want other devices to access this port then you should not set more than two secure MAC addresses.
Below is an example for this configuration:
| Switch(config)# interface fa0/1 Switch(config-if)# switchport mode access Switch(config-if)# switchport port-security Switch(config-if)# switchport port-security mac-address sticky Switch(config-if)# switchport port-security maximum 1 vlan voice Switch(config-if)# switchport port-security maximum 1 vlan access //Configure static MAC addresses for these VLANs Switch(config-if)#switchport port-security mac-address sticky 0000.0000.0001 Switch(config-if)#switchport port-security mac-address sticky 0000.0000.0002 vlan voice |
(For more information about this, please read http://www.cisco.com/en/US/docs/switches/lan/catalyst4500/12.2/31sg/configuration/guide/port_sec.html)
Question 4
Refer to the exhibit. What type of attack would be mitigated by this configuration?

A. ARP spoofing
B. MAC spoofing
C. VLAN hopping
D. CDP manipulation
E. MAC flood attack
F. spanning tree compromises
Answer: E
Explanation
The maximum number of hosts allowed is 5 so an attacker can not flood the switch with many source MAC addresses -> This configuration is effective against MAC flooding attack.
Question 5
Refer to the exhibit. Port security has been configured on port Fa0/5. What would happen if another device is connected to the Fa0/5 port after the maximum number of devices has been reached, even if one or more of the original MAC addresses are inactive?

A. The port will permit the new MAC address because one or more of the original MAC addresses are inactive.
B. The port will permit the new MAC address because one or more of the original MAC addresses will age out.
C. Because the new MAC address is not configured on the port, the port will not permit the new MAC address.
D. Although one or more of the original MAC addresses are inactive, the port will not permit the new MAC address.
Answer: D
Explanation
The port-security aging time is set to 0 so it is disabled for this port -> even if the original MAC addresses are inactive, the port will not permit the new MAC address.


